
Connect With Us & Get In Touch
We would appreciate your kind connection with us and allow us to get in touch with you to understand your requirements and how we can assist. Let us assure you that we would not be spamming you with marketing emails.
Infrastructure
All of our application services run on the cloud. All of our services and data are hosted in Amazon Web Services (AWS) facilities across South East Asia in its own secure network.
1. Cloud Hosting - AWS
With ADAM, we focuses on delivering the best e-procurement software to our customers. We partner with industry-leading companies to handle cloud hosting, employing their expertise and compliance with best practices in maintaining key systems infrastructure such as: DNS, routers, switches, load balancers, computer systems, database servers, caching systems and more. ADAM has selected Amazon Web Services as our providers of cloud services.
Our databases are hosted on the latest-generation database servers on Amazon Web Services. They are hosted across multiple data centers to provide redundancy, safety, and security in storing your data. In the event of an incident with our database cluster, we are able to efficiently and quickly restore from multiple sources of backup and route traffic from the previous database cluster to a new database cluster. Any file attachments are stored on AWS S3 across their SouthEast Asia Data Center network.
2. Compliance
Amazon are pioneers in ensuring safety and security is priority across all of their data centers and infrastructure through their 15+ years of experience of running industry leading web services.
Amazon Web Services are trusted and relied upon all over the world to provide highly secure and scalable infrastructure. Learn more about Amazon Web Services security here, including their System & Organizational Control (SOC) report.
Severity and Expected Response Times
The ADAM team will provide the Customer with support related to server accessibility and performance. This is separate from and in addition to the support services specified in the Support Service Level Agreement (link) and/or the Support Subscription Packages referenced in that document.
Expected response times for a ticket submitted by the Customer via email, phone, or Live-chat request during support hours to report an incident which has been deemed by ADAM (in its reasonable discretion) to be related to server accessibility or performance shall depend upon the severity level assigned by ADAM to such ticket (in its reasonable discretion). Such severity definitions and expected response times are as follows:
1. SERVER ACCESSIBILITY & PERFORMANCE INCIDENT ASSESSMENT
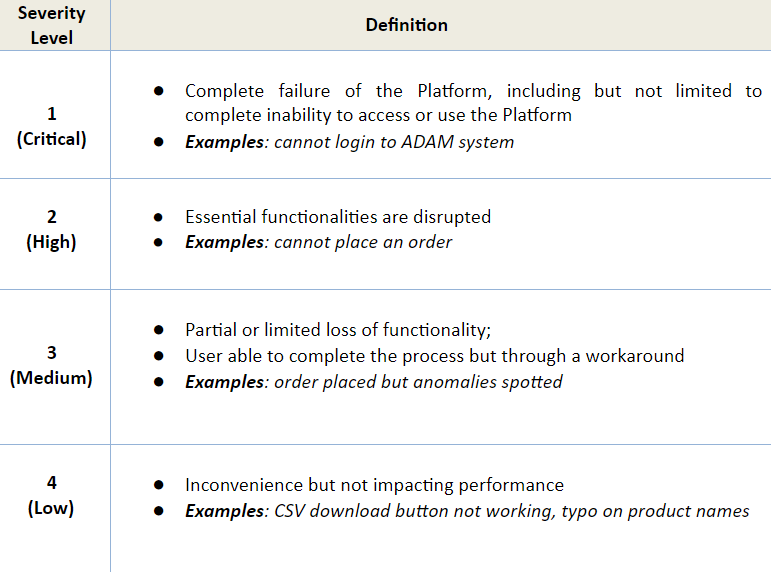
ADAM shall diagnose, respond and rectify the problem within the time frame as indicated below:-
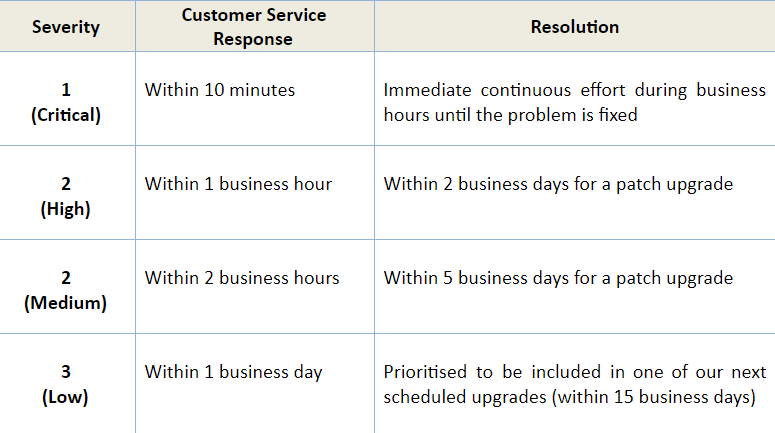
2. Incident Response
In the event of an incident, our Team Members responsible will immediately work towards a resolution. Incidents are grouped as stated here:
Our Data Centers (Amazon AWS) will notify us about any physical or virtual breaches to the equipment that ADAM is hosted on. The ADAM team will respond according to best practices depending on the nature of the incident.
If ADAM detects an Application Level Breach, our Development / Operation teams will immediately investigate. We will determine the cause and affected Customer(s), notify those Customer(s), and restore any backups as necessary.
User- Account Activity Monitoring
1. Personal Data Breach Protocol
If a personal data breach is detected, we will notify our customers without undo delay, at which point the data controller (our customers) have 72 hours to notify the appropriate authorities.
Our personal data breach notice will include as information that is available at the time of the notice. To the best of our ability, we will provide:
Internal Information Security Policies
1. Access Management & Control
Our Team Members are provided access to systems with the appropriate permissions to perform in their role.
They are provided access as needed, any requests for other platforms will have to be approved by their Team Lead.
2. System and Application Access Control
Our main user directory is on Google G Suite (Google Apps for Business) allowing a centralized management of emails and documents created by Team Members. All services that we use are encouraged to go through Google Login (SSO).
For services without Google Login, Team Leads & our internal I.T. team maintains admin control to software systems. This includes third-party SaaS applications, Amazon Web Services.
In our software development team, developers have access to code repositories that they are directly contributors to.
Only our Technical Lead Developer and CTO have the ability to work on production systems that ADAM is hosted on.
3. Prior to Employment
The ADAM team interviews candidates rigorously to ensure that Team Members are able to provide the best performance and care to our customers. Our HR team conducts reference checks.
4. During Employment
Once hired, only systems and software that are necessary for their work are granted to the team member. In addition, Team Members are provided with access to the country they are allocated to eg. Australia / Malaysia / Singapore / Hong Kong etc, access to an access key card to the building and unit.
Termination and Change of Employment
Prior to the change of employment, HR will reach out to our I.T. Team and Team Leads to ensure we are ready to go through an “off-boarding” process to revoke user credentials and access control.
This includes: G Suite Login, Software Credentials, API Tokens and access cards revoked from the User.
During the exit, our HR Manager will also ask for any property of ADAM to be returned immediately. Any outstanding tasks will be handled by the Team Lead.
Data
Data security and privacy are serious concerns at ADAM, and we know they’re also important to our customers. Although we can’t tell you everything about our data security and privacy practices or disclose the specifics (that, in and of itself, wouldn’t be secure), we do want to address some of the most common questions we receive.
1. Data Transfer
Any data transfer between you and ADAM’s Web Application is done using a secure 256-bit HTTPS (SSL) connection. We employ SSL to protect your documents, passwords, and interactions with ADAM from eavesdropping.
Our application and database servers are hosted within Amazon Web Services (AWS). Data transferred within AWS is done securely within a private network. Additionally, our application and database servers are behind firewalls that allow specific access and privileges to services. For example, our application servers are allowed direct access to the database server cluster through the network & user credentials.
2. Data Storage & Retention
ADAM keeps data for active customers of the platform. Historical procurement transaction data & documents over the last 7 years are stored securely across data centers at Amazon Web Services.
We employ single multi-tenant database systems with API authentication & authorisation to ensure that only you will have access to your data when using ADAM.
We encrypt your documents and all information stored in our databases at rest. The data is encrypted using AES-256
If a customer does not renew their ADAM Subscription, the customer will have 120 days to export data from the platform. ADAM will remove data from inactive customers after the 120 day period.
3. Data Loss and Corruption Prevention
To keep your data safe and separate from other ADAM users’ data, your data is hosted within a master database that separates customers’ data via access controls.
Our databases are always stored using highly redundant replicated storage and additional daily backup strategies.
4. Authentication
Users of ADAM must go to their specific web application URL to login with their credentials. Logins can be achieved only by using an email (that has been verified) and password. Administrators of the ADAM instance have the ability to manage user credentials, roles, and revoke access as necessary.
Based on the user role(s) that are assigned to a user, the system will show the appropriate pages that can be accessed. If the user tries to access different pages through different links, they will be redirected to an error page stating that they do not have the proper permissions to access that page.
5. System Performance
ADAM wants our customers to have the best experience when using our platform and services. We have designed our platform to have multiple redundancies and distributed systems.
At the start, there are multiple application servers that sit behind a state-of-the-art load balancer that routes traffic to an application server with the most resources available to serve requests. Similarly, we run on the current generation database server clusters that are able to serve heavy traffic loads.
In the result of a failure, our systems will automatically re-adjust and re-route traffic to the appropriate systems.
In the event of a complete failure, we have the ability to restore the system from other infrastructure using system scripts to rebuild servers.
6. Data Access
Only authenticated users can access your ADAM Instance. Any objects created (purchase requisitions, orders, analytic reports) are tied to the specific logins with the details, comments, and attachments. Changes that are made in the system are logged in an audit log with details on the action, previous information stored, and new changes.
Software Development & Quality Assurance
Our software team follows the best practices recommended by the Scrum Alliance, outlined in Agile Software Development. The Scrum Masters and Product Owners are trained on how to execute proper requirements planning, design, developer sprint planning, delivering code based on the requirements and our internal definition of done (code quality, unit tests, code review, and review by our Product Management Team), quality assurance, staging, launching to production, and sprint retrospectives for our Software Development Lifecycle (SDLC).
1. Development
As products are in development, each developer is given the necessary & most efficient resources to run the application in a local environment. Developers work within this environment and push code changes to a centralized and secure code repository.
2. Staging
This environment allows our Quality Assurance team to test the latest work, reported bugs, and performance improvements.
A Quality Assurance Member will review the work of the developer and test their work on a staging environment that is hosted on AWS. This allows for our Quality Assurance team to test for any issues or failures and request fixes before deploying the system to production.
3. Production
Production systems environment access is restricted to our Technical Lead Developer and CTO. They are able to administer, monitor, and make improvements to the infrastructure. They are responsible to ensure uptime of the system.
4. Test Data
In order to address customer-specific issues, our Quality Assurance Team may request environments that replicate The Customer’s interface.
Your Role in Ensuring Security
Protecting your assets is a team effort between you and ADAM, and we take this partnership very seriously. As such, we feel it is critical to help you do your part. Security is a tough balance between protection and efficiency. Just as military fortifications are very secure, they are hard to enter and exit. The additional procedures that secure the facility effectively slow down operations within. That being said, we want to provide you guidance on measures that you can take to improve your protection, and still meet your business needs.
Here are some simple steps that every ADAM user should employ:
Further, we encourage our customers to assess their own, individual data protection needs. For example, if you require additional data protection, you can use third-party encryption systems to encrypt documents before uploading them into ADAM.
SECURITY FAQ
2. Can the system support the ability to associate each user to one security role?
Yes, the system allows implementation of role based security measures and access rights management.
3. How do I know that my documents stored in ADAM will always be available? What is the SLA?
The ADAM Service Level Agreement is 99.4% uptime to ensure anywhere, any time access to your documents.
4. How often is the data that I store in ADAM backed up?
ADAM maintains copies of your files both in its live data center and in offsite archives. Redundant copies of your files are created after you upload a file. Further, archived copies of your files are created within 24 hours after upload.
5. Where Do I Report Security Concerns?
Our top priority is making ADAM safe for all of our users. While we’re very confident in our security technology, we prefer to investigate any and all reported security concerns with any of ADAM’s software.
Please report security problems or questions to hello@adam-procure.com
Document Last Updated : 27th April 2023